|
Over 50% of emails sent to your address are spam. Over 50% of computer viruses are contracted via email phishing and over 60% of phishing emails are ransomware! What is phishing? Phishing is like fishing but by way of email. Put some bait on the hook and see what you catch. Sometimes the bait is irresistible, often appealing to your desires, important work matters, or threats. Attempts can be incredibly clever and often difficult to discern from a legit email. I'll try to offer some basic guidelines to follow. Imperative. Be suspicious of everything! Be vigilant. THEY are out to get you. Now is the time to employ that paranoid part of your personality. Some general Rules to keep in mind.
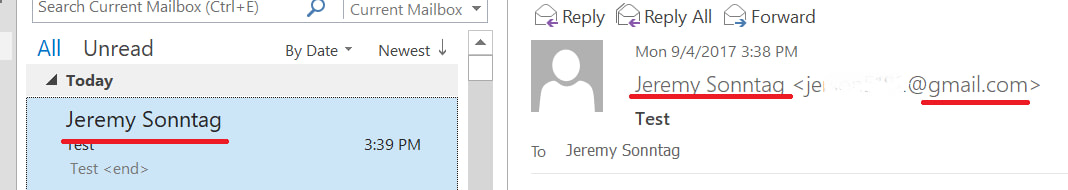
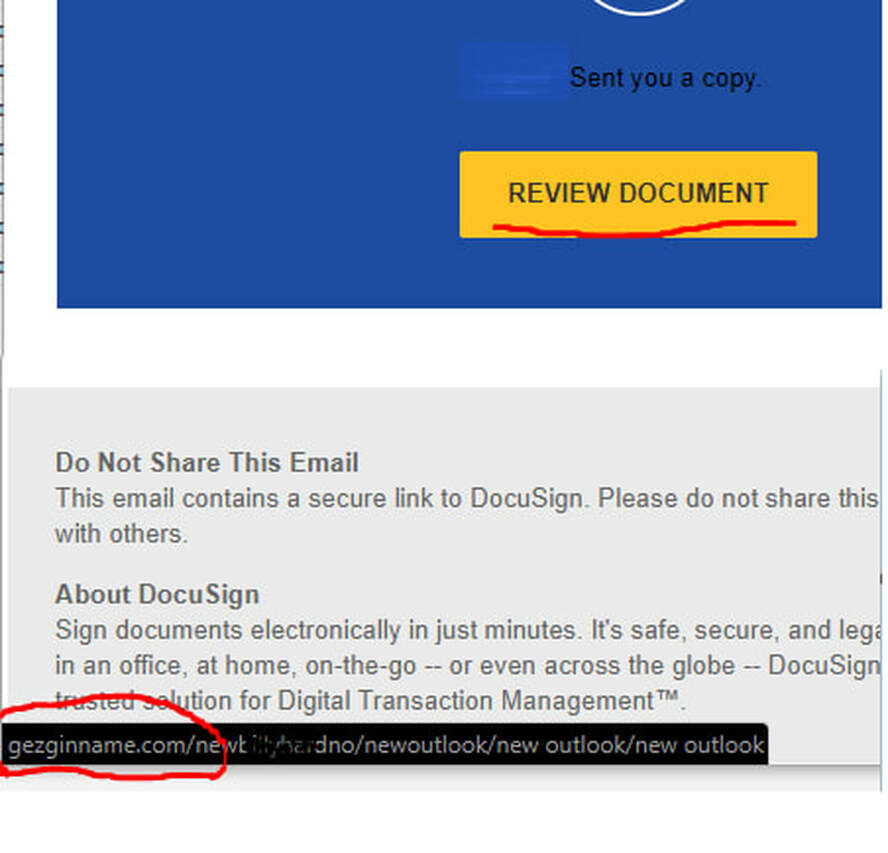
Identifying a phishing email If an email is making a request of you, consider the possibility that your reply reaches a stranger with malicious intent. Be aware that such attempts occur continuously, practically an organic piece of the internet. Spoofed sender address There are many ways to "Spoof" or fake the sending email address. The simplest, yet still effective method is to create a Gmail or other free email account with the desired name. Anyone can create an email account with a free email provider using any name they choose. There is no verification process to prevent it. Outlook and other mail applications will show the full name then in smaller print and sometimes not at all, the actual email address. It's easy to miss this if you're not paying attention. This is a major reason businesses do not use free email accounts such as gmail. Anyone can use this technique to send an email as your CEO demanding some sensitive data. You may feel tension, eager to please the boss and happily offer up this precious data. This happens all the time and is only stopped by making everyone aware. Links in emails There can be various motives when it comes to links in emails. I'll describe the two most common. First, the spammer may send you an email insisting you login your account, email, banks, etc. They will then have a website setup that looks just like the real website but it is hosted on their own server. When you happily enter your password to gain access, you are providing this info to the attacker. Second, an email link may direct you to a download or a website with some evil Javascript, no doubt resulting in a nasty virus or data stealing element. Some Other things to note: Keep links in mind everywhere. Social media, text messages, even webpages. Also, be extra cautious with shortened links. These look like "bit.ly/a3f02e" which redirect you to the actual destination. These types of links can be useful in social media but are inconspicuous by nature. Identify misleading links. Hover you mouse over the link and check the "status bar" at the bottom for it's destination. So if the link claims to be Wells Fargo but the URL is NOT wellsfargo.com, you should stay away. Attachments Simply put. Attachments are dangerous. Always be on your guard with email attachments. If anything seems abnormal, DO NOT open the attachment. Any attachment can masquerade as something harmless, a PDF, excel sheet or picture. All of these can be used to covertly install a virus. Confidential Information Information can be worth a lot to someone who knows how to use it. You would think it is common sense to not reveal sensitive information but spammers can be extremely clever. Do not negotiate money transactions over email, especially when it involves the account / routing numbers. Do not send passwords or other account info for any of your accounts. Do not send personal data. SSN, driver's lic, Credit card info, etc. All of this type of data is risky to send over an email but the risk hugely increases when you are replying to a request for this type of info. Even if everything looks legit, you have no means to identify the sender. I understand it is convenient, But for these cases, Find another means. Wrap it up Email is the easiest way to get access to you and your computer. For that reason, email is the most used vector to try and exploit you and your computer and your company. Stay aware and proceed with caution. AuthorJeremy Sonntag - NetCertPro
0 Comments
|
AuthorJeremy Sonntag & Archives
November 2019
Categories
All
|
|


 RSS Feed
RSS Feed
